Timing attack
Summary
- Timing attack is considered one of the most serious threats to cryptographic products;
- Most adversaries need physical access to the device and expensive hardware to carry out a cryptographic attack. However, some adversaries strike with timing attacks, needing no physical access to a device and using only software tools;
- A typical timing attack goes as follows: an attacker gets remote access to a vulnerable program over the Internet, they supply various inputs and time the processing, then they statistically analyze the time measurements and supply new inputs, trying to gain more information with each input..
More on the topic
The threat of side-channel attacks is as real as never before.
The threat of side-channel attacks is as real as never before.
Even theoretically robust and well-studied cryptographic solutions can be vulnerable due to faulty implementation.
Side-channel attacks aim at obtaining sensitive information (the key) through the measurement of some physical quantity while the faultily implemented program is running.
Measurable quantities include power consumption, electromagnetic radiation, the running time of an algorithm etc.
Measurable quantities include power consumption, electromagnetic radiation, the running time of an algorithm etc.
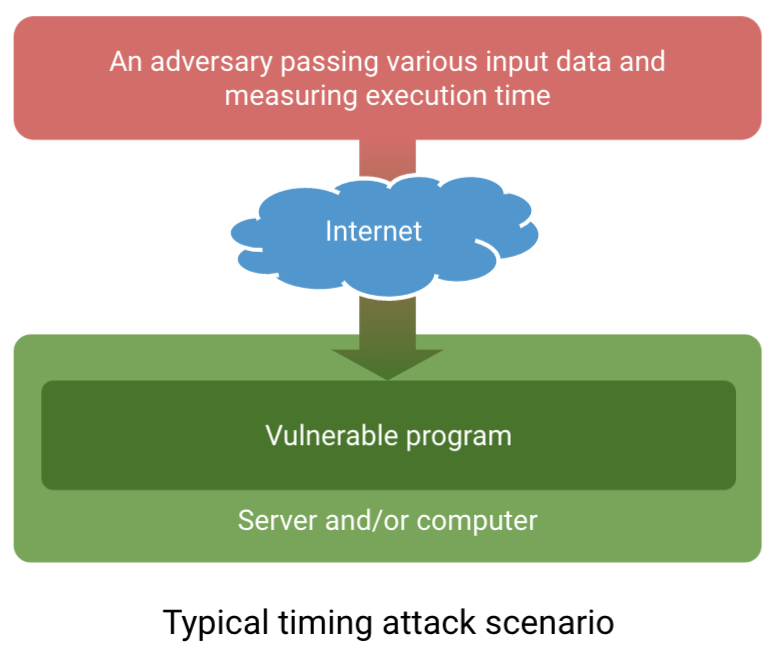
A typical timing attack.
Timing attacks to look out for when developing cryptosystems
Timing attacks became widespread after Paul Kocher's 1996 article. Countering timing attacks is rather challenging – running time has to be independent of sensitive data, meaning that developers have to be highly competent and adhere to non-standard coding practices.
Since timing attacks are rather difficult to defend against, there are similar vulnerabilities found in almost every cryptographic library. According to the Common Vulnerabilities and Exposures (CVE) system, thirteen vulnerabilities rated Medium and four rated Low were found in OpenSSL, the most popular software library. Some of the attacks have already been described (Paper 1 and Paper 2).
Timing attacks became widespread after Paul Kocher's 1996 article. Countering timing attacks is rather challenging – running time has to be independent of sensitive data, meaning that developers have to be highly competent and adhere to non-standard coding practices.
Since timing attacks are rather difficult to defend against, there are similar vulnerabilities found in almost every cryptographic library. According to the Common Vulnerabilities and Exposures (CVE) system, thirteen vulnerabilities rated Medium and four rated Low were found in OpenSSL, the most popular software library. Some of the attacks have already been described (Paper 1 and Paper 2).
The most damaging attacks are Spectre and Meltdown. Due to hardware vulnerabilities in processors, timing attacks make it possible to obtain various sensitive information. The reasonable conclusion is that timing attacks should not be underestimated, and even the most competent developers and engineers can make mistakes.
How to protect your hardware and software against timing attacks?
Take a closer look at our software application TAF (Timing Attack Detecting Framework).
Take a closer look at our software application TAF (Timing Attack Detecting Framework).

