TAF v2.1
Timing Attack Detecting Framework in cryptographic products.
Improving the security of hardware and software solutions.
Improving the security of hardware and software solutions.
One of the most serious threats in the development of cryptographic projects arises from the possible implementation of a timing-attack.
For most attacks physical access to the device and expensive equipment is required. However, among side channel attacks, timing attacks stand out, for which measurement can be done using only software tools and also without physical access to the device.
For most attacks physical access to the device and expensive equipment is required. However, among side channel attacks, timing attacks stand out, for which measurement can be done using only software tools and also without physical access to the device.
Since the vulnerability of a function may depend on the compiler and platform, testing should be performed on the target compiler and platform.
Necessary condition for a timing attack is a dependence of the execution time on secret data. TAF aims to determine if such a timing leakage is present in the program under test.
At the output, the framework provides an answer whether the attack was detected, as well as statistical data that can be used to find out, for example, how easy it is to detect an attack (which means it is easier for an attacker to exploit it).
At the output, the framework provides an answer whether the attack was detected, as well as statistical data that can be used to find out, for example, how easy it is to detect an attack (which means it is easier for an attacker to exploit it).
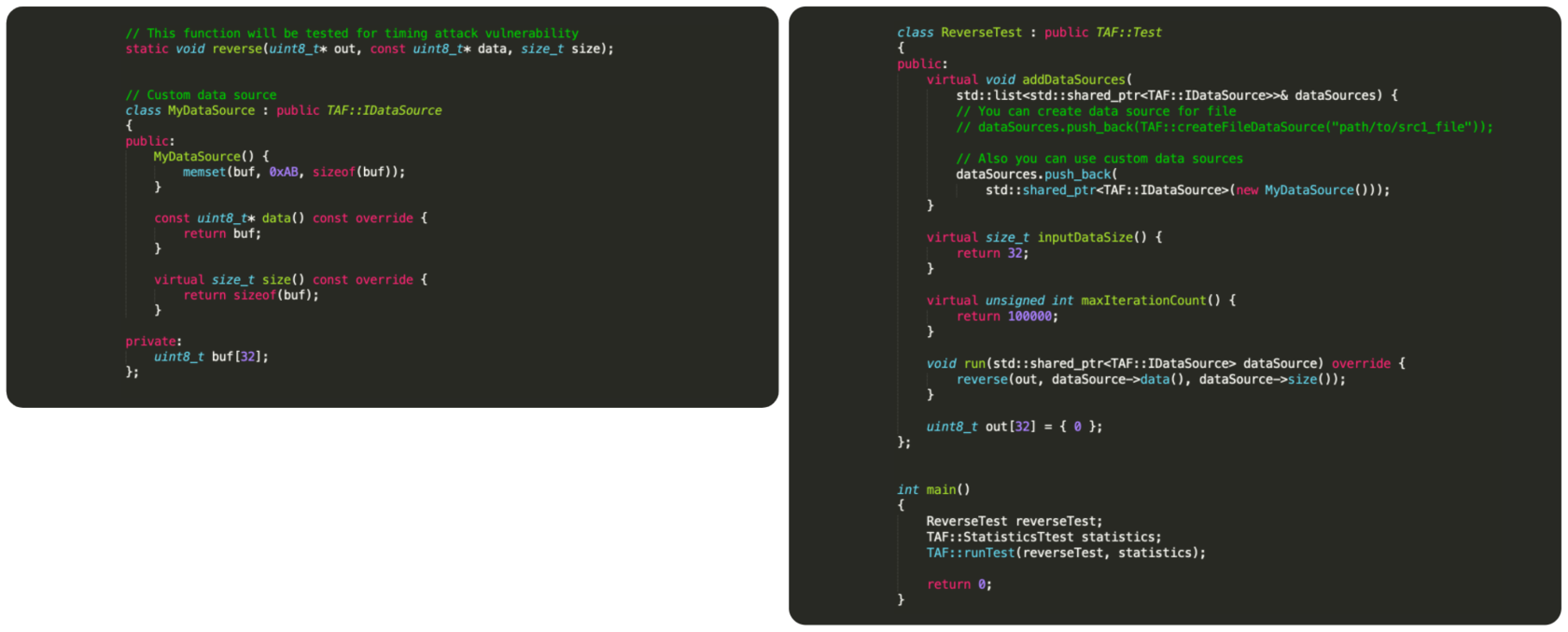
TAF is implemented in C++ with maximum ease of use in mind
The user needs to define 2 classes that describe how to run the function under test and what the input for the function is.
Stages of TAF usage
The framework needs «good» input data to work well. TAF uses a fuzzer to get these inputs. An additional bonus of this stage is testing the program for various bugs.
Using one of the inputs, the TAF receives two sets of measurements. The first includes measurements of the execution time at the selected input, for the second set a new random input is used on each measurement. These measurements are then processed for use in the next step.
A statistical test helps determine whether these sets of measurements can be distinguished from each other. The test returns the probability that these samples are drawn from the same population, i.e. they can't be distinguished.
Based on the result of a statistical test, it is determined whether it is possible to make a conclusion about the presence or absence of an attack, or whether it is necessary to collect more measurements.
If an attack is detected, it is necessary to manually analyze the code and fix the vulnerability. To more accurately determine the location of the vulnerability, you can test the subfunctions of the program.
TAF key advantages
The framework is not aimed at automatically constructing timing attacks, instead it tries to find a timing leakage, on the basis of which an attack is potentially possible.
Since the framework is based on direct measurement of the program execution time on the target platform, it takes into account all possible causes of leaks (program branching, cache, timing variation of processor operations, such as multiplication or division).
Since the framework is based on direct measurement of the program execution time on the target platform, it takes into account all possible causes of leaks (program branching, cache, timing variation of processor operations, such as multiplication or division).
2 types of statistical tests are used:
Welch's t-test — the most popular statistical test, in many cases it performs better than others.
Kolmogorov-Smirnov test — a more general test that uses fewer assumptions. It can in some cases detect an attack faster than Welch's t-test.
Convenient API
TAF is capable of testing for higher orders of attacks (with such attacks, techniques such as masking can be bypassed).
Testing that the compiler and platform being used will not introduce a vulnerability to otherwise secure code.
Fuzzer generates input data.
Delivery set of API TAF
Fuzzer and instructions for working with it for the needs of the framework.
TAF in the form of a binary library and a set of header files.
Documentation.
Algorithms that can be used to verify correct work of the framework (Includes a vulnerable and secure version of the memcmp function, as well as a vulnerable AES implementation)
Accompanying services

