Quantum threat
Synonyms: Quantum computer attack, attack by quantum computers, quantum attack
Summary
- Quantum threat is a risk associated with an attacker gaining access to data encrypted using traditional methods as a result of a quantum computer-based cyberattack;
- Fundamentally new circuitry and operation logic allow new generations of computing devices, i.e. quantum computers, to compromise existing information security protocols;
- Over the next few years, many traditional cryptographic algorithms, such as key distribution, asymmetric encryption and electronic signatures, will become entirely obsolete.
More on the topic
To utilize information technology, one needs to necessarily ensure data security, i.e. its confidentiality, integrity and availability. Most existing methods of maintaining data security are based on public-key cryptography: while data is encrypted via simple mathematical operations, cryptanalysis still requires enormous computing resources.
The appearance of a new computing device generation, i.e. quantum computers, poses a challenge to modern cryptographic algorithms.
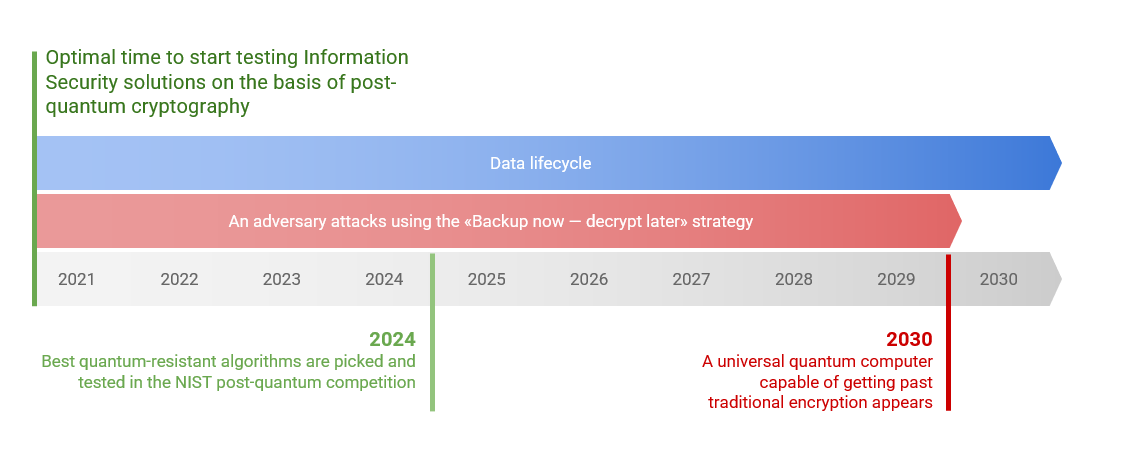
Adversaries can already backup data encrypted by traditional methods, waiting to decrypt it when they have access to quantum computers.
To utilize information technology, one needs to necessarily ensure data security, i.e. its confidentiality, integrity and availability. Most existing methods of maintaining data security are based on public-key cryptography: while data is encrypted via simple mathematical operations, cryptanalysis still requires enormous computing resources.
The appearance of a new computing device generation, i.e. quantum computers, poses a challenge to modern cryptographic algorithms.
Adversaries can already backup data encrypted by traditional methods, waiting to decrypt it when they have access to quantum computers.
In particular, Shor's algorithm makes it possible to efficiently solve factorization and discrete logarithm problems, while the complexity of these problems accounts for the robustness of such cryptographic primitives as RSA and ECDSA, which are at the core of most cryptographic data protection methods. In addition to it, Grover's algorithm makes it possible to search through an unsorted database exponentially faster than even the best of classic algorithms can. Therefore, it is necessary to reconsider the security requirements for symmetric encryption algorithms. Due to continuous progress in quantum computing, implementing Shor's algorithm is gradually becoming possible for more devices.
Thus, now there is a clear need for introducing new algorithms resistant to quantum computer attacks into the widely used cryptographic data protection framework. An adversary can steal classically encrypted data without quantum-threat protection if they have access to a quantum computer. Both science and business communities, along with international cybersecurity regulators, are now actively discussing the necessity of switching to quantum-resistant encryption methods.
Thus, now there is a clear need for introducing new algorithms resistant to quantum computer attacks into the widely used cryptographic data protection framework. An adversary can steal classically encrypted data without quantum-threat protection if they have access to a quantum computer. Both science and business communities, along with international cybersecurity regulators, are now actively discussing the necessity of switching to quantum-resistant encryption methods.
Numerous scientific and marketing studies have confirmed the need for local and global markets to implement post-quantum cryptography solutions. International consulting and auditing companies recommend revising long-term information protection protocols because of the possible appearance of quantum computers.
There are two possible data protection strategies one can adopt to avoid a quantum computer attack:
- Quantum communication strategy implies a transition to hardware that uses individual quantum states of light (photons) for transferring encryption keys. There are several limitations this strategy can face, including sophisticated infrastructure, equipment and integration costs and a complicated certification process.
- Post-quantum cryptography comprises new encryption algorithms resistant to quantum computer attacks. Solutions based on post-quantum cryptography are generally cheaper, faster to integrate and easier to update.
Areas most vulnerable to quantum threats:
- Personal data;
- Financial data;
- Medical and genetic data;
- The Internet of Things data (including the Industrial Internet of Things data and the Internet of Vehicles data);
- Blockchain economy data.
How to identify the risks associated with quantum threats and ensure efficient protection:
- Learn more about quantum threats and industry-specific protection mechanisms.
- Conduct an audit of your company's current cybersecurity infrastructure, pick the best quantum threat protection solutions, and develop a protection strategy.
- Pilot quantum-resistant solutions and scale up accordingly.

